Designer Integration (2025.1)
The Designer Integration module allows user to authenticate themselves in the Designer when using a 3rd party SSO.
If you are using a 3rd party SSO, the standard OAuth2 mechanism does not provide a convenient and secure way for client software that is not web-based to authenticate.
This module allows Ambience servers using 3rd party SSO to use the web to generate a unique temporary token that can be used in place of user credentials within the Designer client application.
The feature allows the convenience of managing users within the 3rd party system, while still allowing the client software to authenticate and gain access to the server functionality. You don’t need to use this module if you are using Ambience SSO (though you can, it still works the same) because Ambience internal SSO has additional support for client authentication.
This module is available for both Ambience and Repertoire software suite.
Module Interface
| Interface | Description | Required Privilege |
|---|---|---|
| Designer Integration | Allows Designer Integration access. | mod-designer-integration |
Generate Token
To generate a request authentication token, click on the “Request Authentication Token” button in the Designer Integration page.

A token will be generated. Note down the token and add it to the Designer.

Click on the “Finish” button to refresh the page.
Add Token In Designer
Launch the Designer and click on the “Connect” button at the top. A “Connect to http://localhost:1740” dialog box will appear.
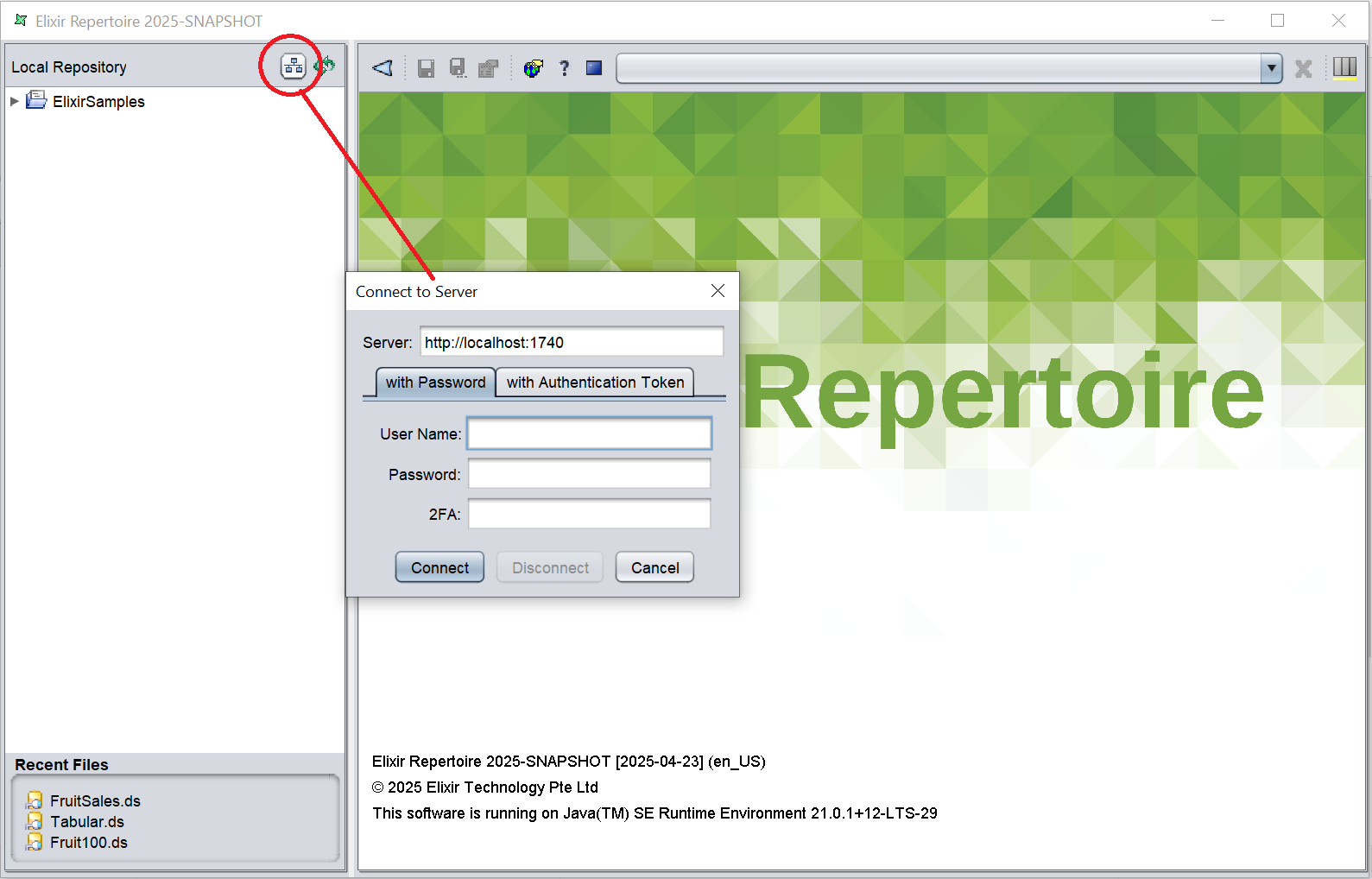
Select the “with Authentication Token” tab in the dialog box.
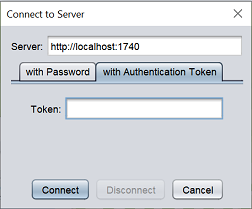
Enter the token generated from the Ambience Designer Integration module. Click on the “Connect” button to connect to Ambience Repository. Once connected, the Designer will display the content of the Repository in Ambience.
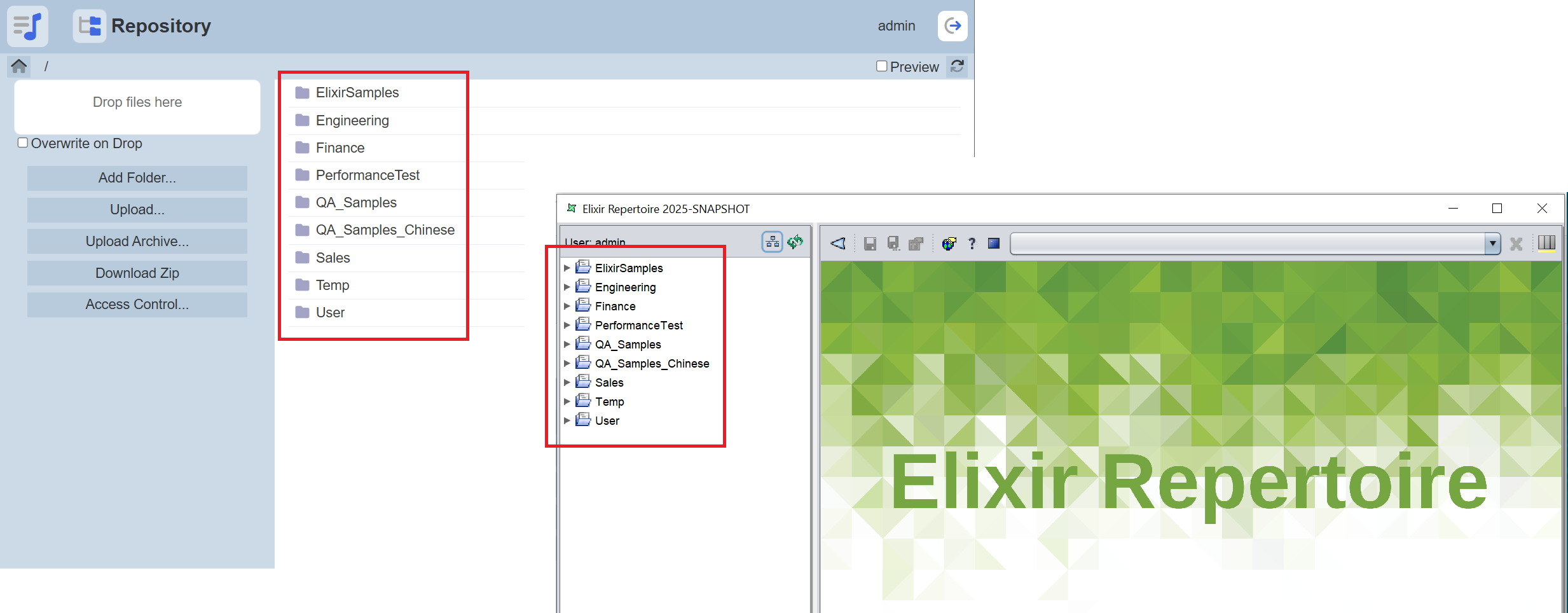
Do note that the token is valid for five minutes and for one time use only. That is, if the server is disconnected, the same token cannot be used to connect to the server again. The list of folders and files in the Repository depends on the privileges of the user who generated the token.
